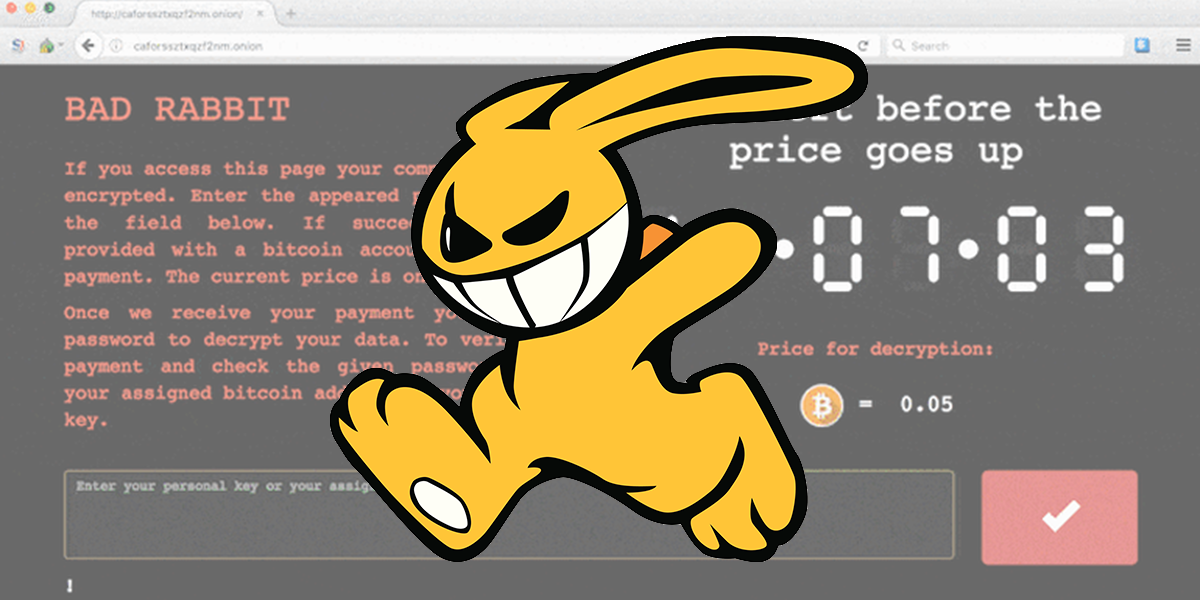
He’s been making waves over the past few days at Bad Rabbit, even though it’s not exactly Easter season. Unfortunately, this is yet another ransomware that is spreading in Europe and started from Russia and Ukraine like the previous Petya and NotPetya. The first organizations affected by Bad Rabbit include Ukraine’s Ministry of Infrastructure and Kiev’s public transport system and, in Russia, news services Interfax and Fontanka.ru as revealed by Kaspersky Lab. The well-known IT security systems company puts corporate networks, which seem to be in the crosshairs of Bad Rabbit, on alert.
Bad Rabbit presents itself through request to download and run infected installation files but covered by a fake name, a fake Adobe Flash Player, which has long been in the crosshairs of cyber criminals, who find holes in software and use them to attack users or hide malware. About the creators of this ransomware it is supposed to be fans of the Game of Thrones saga given the references to the characters Daenerys Targaryen and Grey Worm.
As in the most classic ransomware, Bad Rabbit-infected computers direct the user to pay a ransom of about €250 (0.05 Bitcoin) in exchange for the data and with the usual countdown clock ticking down the time before the required amount is increased. Obviously, post-payment data delivery is not certain. What makes this malware so dangerous compared to any ransomware is the speed with which it propagates through vulnerable email attachments or web plugins. Early indications suggest that it contains the same “password stealing” tool as NotPetya, allowing it to paralyze any company in no time.
How to prevent? Amit Serper, a security researcher at Cybereason, claims to have found a vaccine for the attack, which should completely prevent Bad Rabbit from infecting your computer (step-by-step instructions are available on Cybereason‘s website).
In principle, let’s briefly recall three key steps to limit the possibility of any cyber attack:
- Keep your software up-to-date by downloading the latest updates;
- back up regularly including at least one offline and encrypt the backup;
- make use of multiple layers of protectionto lower the likelihood of attack.
Sara Avanzi