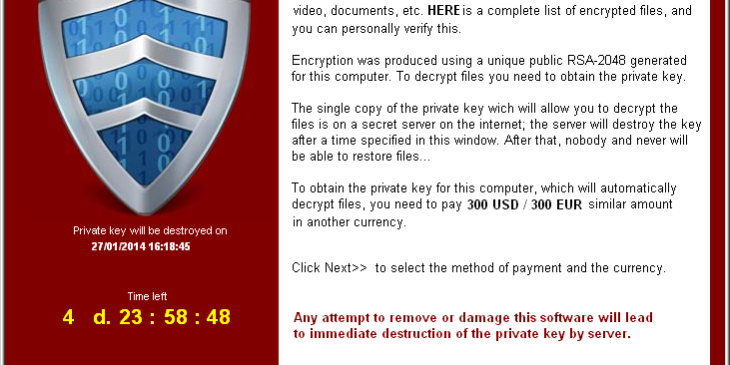
For the past three years a new cyber threat has been gaining ground: it is CryptoLocker, a powerful virus that has the ability to encrypt the files of its victims’ Windows PCs and then demand a ransom payment to get the files back. Cases of CryptoLocker infection have drastically increased in the last year, as the virus itself has evolved to its third generation called TeslaCrypt 3.0.
Awareness of what this threat looks like is a basic aspect of avoiding it. The dissemination method adopted by CryptoLocker TeslaCrypt 3.0 is email, specifically via attachments or links contained in the same email message. The main trap is that the email appears to be sent by a friendly contact. However, there are signs that we can pick up to avoid being infected – in addition to having a good antivirus at our disposal. Usually, emails with which TeslaCrypt 3.0 is transmitted not only contain topics that are of no interest to the recipient, but also sloppy text: missing text, grammatical and form errors. If it’s an attachment, it’s a good idea to check whether the sender of the message is actually waiting for some kind of document: if so, pay close attention to zipper files. Another aspect that should not be underestimated and that can help us to avoid the TeslaCrypt 3.0 threat concerns the recipients of the email: keep an eye out if the email is not addressed only to us but to a list of contacts!
Unfortunately, currently no solutions have been found yet to decrypt the data and not even the ransom payment ensures the return of the data. However, we can prevent unpleasant situations like these with Backup. The IT solution staff presents the Synecaresystem, a UTM appliance that integrates in a single hardware solution, a Smart firewall with antivirus, antispam and access control, an advanced storage solution and a 3CX central unit.
In case of CryptoLocker infection, immediately disconnect all peripherals connected to the machine and do not hesitate to contact us!